Welcome to the official CrococryptMirror Homepage:
Encrypted File Backups
CrococryptMirror is a free software without registration, without activation, without limitations and without ads.
Introduction
CrococryptMirror (aka "Crococrypt") is an encryption tool which mirrors complete folders to encrypted folders. The encryption algorithms that are used are AES and Twofish (256 bits, cascading). The keyfile is secured by a password using PKCS #5 (PBKDF2) with a SHA512/Whirlpool based HMAC using 100000 iterations and also AES and Twofish.
Additionally, a ZIP compression for storage space optimization is used. For reasons of performance the synchronization of source and destination folder is done in the background.
A backup copy of the keyfiles has to be stored at a secure place. Without the keyfile the containers cannot be decrypted.
In the portable version of CrococryptMirror keyfile and settings are stored together with the application folder. Hence, the complete application can be transported on an external storage device. Moreover, the folder "container" can be used to store portable containers.
Mirroring can be done manually (on-demand) or by using the sync service which detects directory changes on the fly.
Features
- Copying and synchronizing of arbitrary folders/directories to encrypted folders (Backup Containers)
- Automatic Synchronization (Live mode, e.g., for Cloud Uploads)
- On-Demand Synchronization (e.g., for external drives like USB drives)
- Encryption of file content, filenames, file meta data
- Shorten of filenames
- Using the highest encryption standards (AES-256 & Twofish-256) and password security techniques (PBKDF2, SHA512 & Whirlpool, 100000 iterations)
- Especially the password security implementation is flexible and can be adapted in the future to fit current hardware performance issues
- Source folders can be stored in multiple destination containers at the same time (e.g., USB disk drive and Cloud storage)
- Network drives can be used as sources and destinations
- Encrypted containers can be read through the Explorer View or through Batch decryption
- Portable Version
- No administrative/system rights necessary
- No installation, everything in one directory (Application & Data)
- Can be used independently of the manufacturer (HissenIT): No registration, no online service, no online activation
Use Cases
Some use case and feature examples:
Encrypted Cloud backup
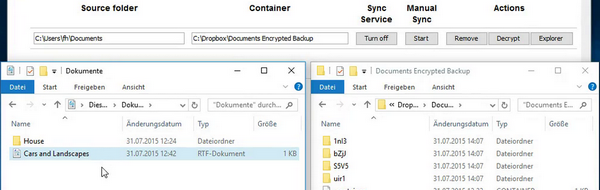
Mirroring of folders on your computer into your cloud storage folder in encrypted form.
Encrypted backup on USB drive
Mirroring of folders on your computer to an external storage device in encrypted form.
Encrypted multi-backup
Multiple storage locations can be used in parallel, e.g., an USB drive, Cloud storage and a local NAS. When using the sync service all encryption destinations while be queued and processed sequentially.
Two encryption modes
Use the automatic sync service or mirror a directory on-demand simply by clicking on CrococryptMirror's tray icon. Use the latter if you work constantly on a certain directory and do not want to create to much load for a backup.
Synchronizing means that also deleted files will be deleted in the container's destination, at the end both directories have the same content. The source directory is not touched.
Two decryption modes
A complete directory can be efficiently decrypted in a bulk operation. When only single files shall be restored, the Explorer view can be used. For this purpose, a local WebDav view on the encrypted container is opened (read-only), so files can be browsed and copied.
Technical Background
For technology enthusiasts, we want to describe some implementation details. CrococryptMirror uses two well-known cryptography providers: Oracle (originally Sun) for AES and Bouncy Castle (open source) for Twofish. These are popular implementations, the cryptography is done using these providers not by implementing the algorithms myself. On computers with CPUs which include AES hardware support, this AES implementation is used automatically. This is also done by other popular encryption tools today.
By using two different encryption algorithms and different implementations, the risk of compromising the whole encryption scheme is minimized. For instance, if you store an archive of your personal data in a cloud storage for a very long time, it might happen that weaknesses in the algorithms itself come up or that security vulnerabilities in the implementations are discovered.
The iteration count of 100000 used for the password protection of the keyfile is upwards compatible with future versions and is not hard coded, for maximum flexibility.
Pro Version
To finance the freeware project, we have introduced a Pro version of CrococryptMirror for a small fee. New features of CrococryptMirror will always be introduced in the Pro version first.
Roadmap
These are simply feature ideas, there is no implementation schedule for the freeware version. Nevertheless, we like to hear your suggestions and are happy about your support.
Idea backlog
- Operating systems: Linux, MacOS, maybe Android app
- PKCS #11 Support: Hardware tokens/SmartCards via P11
- Single File Encryption: (With Explorer menu integration)
- Signing the keyfile: Integrity protection
- File filter: Optional mode for containers to exclude files with certain filename patterns from synchronization
- Quick-Mode: Optional mode without compression and Twofish to make use of AES hardware support on certain Intel computers to speed up encryption (and lower memory consumption)
- Crypto settings: Offer the user to choose between algorithms and options to create preferred (but still secure) cryptographic settings
- SMB/CIFS support: Server version of CrococryptMirror (maybe including group encryption) based on SMB/CIFS
- Commandline interface
Share
![]() Please like and share the Facebook page to spread the product if you like it! This encourages the further development!
Please like and share the Facebook page to spread the product if you like it! This encourages the further development!
If you like CrococryptMirror, it would be a great thing if you share it with others to support its further development!
Keywords
encryption, password security, password based encryption, file encryption, folder encryption, sync, cloud, encrypted file mirror, group encryption, symmetric encryption