Internet Security: Why cryptography (and encryption) is essential
Added at 06/03/2019
Internet connections are no direct lines. Every intermediary component holds full access to your Internet traffic. That means: read, alter, redirect, discard. Or put another way: manipulate, record, log, render unusable.
I deliberately write cryptography because nowadays the expression includes much more techniques than just encryption - meaning providing confidentiality. Providing secure communication cannot be accomplished solely by a common encryption method. However, the details here are not subject of this article. The interested reader should know that HTTPS connections (meaning HTTP over TLS respectively SSL) are cryptographically secured and that encryption methods are part of this protection among others.
Why is cryptography-based protection of our Internet traffic to essential?
To understand the question, you have to understand the basic structure of the Internet.
The Internet – its most popular application being the "WWW" / "World Wide Web" – is simply put an association of many, worldwide computers whose communication follows certain rules – also called protocols.
If you go to a website, you computer tries to contact another, faraway computer – also called server. This does not happen through a direct line but with the help of multiple, in-between computers that can provide a connection to the actual destination – the website.
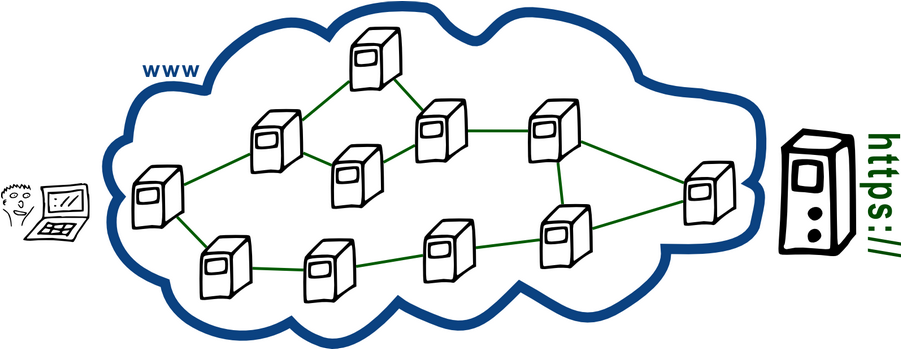
The Internet is a so-called "best-effort" net. That basically means that there is never a guaranteed connection. Algorithms and protocols are responsible to provide a solid connection to the destination computer. You can see that this concepts works great by looking at the obvious success of the Internet itself.
In case that computers on the way to the destination break down, new ways are automatically established. A new "route" gets calculated. This is why we call it "routing". By the way: Even for a single procedure, request and answer do not have to take the same (inverse) way within the web.
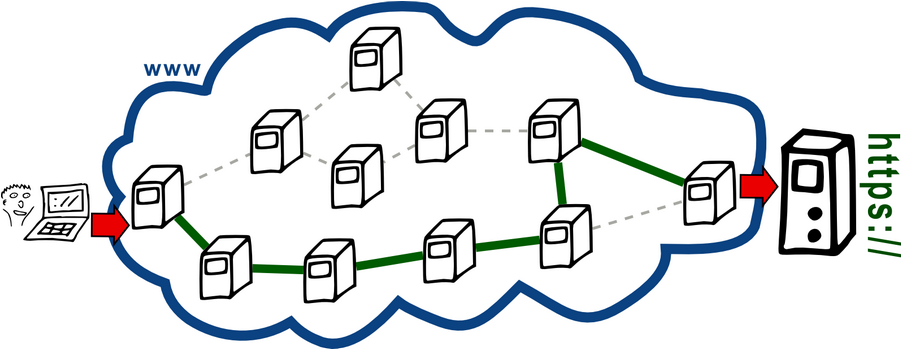
So, between your own computer and your destination exists an unknown and changing number of computers. There is a simple method to uncover some of these intermediate stations – I use a Google search as an example (my location is in Germany):
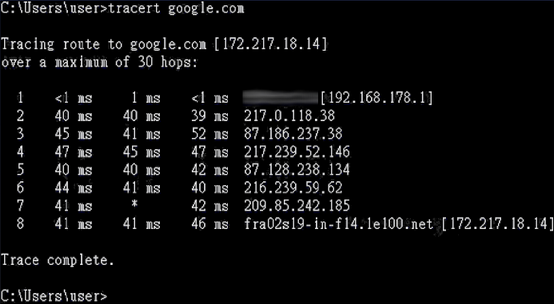
The same is true for, e.g., your online banking or web shops etc. Of course, this applies to every form of Internet protocols and services, not solely HTTP(S): e-mail, WhatsApp, FTP, backends of mobile apps etc.
As you can see in the example, a lot of unknown computers are involved when transmitting the data, not only your own Internet Service Provider (ISP). Every single one of these computers has access to the transmitted data. What is also very important: These are only the VISIBLE Internet components. Other communication devices like cable connections, routers, backbones and other controllers might not be detectable.
However, looking solely at the visible systems: Any of these computers has full access to your Internet traffic. That means: read, alter, redirect, discard. Or put another way: manipulate, record, log, render unusable..
Cryptography and Encryption
This is why cryptographic tools are essential to protect from malicious accesses. Why essential? - Let's just take online bank transfers, phone calls, e-mail communication, logging favorite website visits or accessing files in private cloud storage as obvious examples.
There are various reasons how and why intermediates access transferred traffic. For instance, an intermediate system could be hacked. Regular personnel like administrators could abuse access for different reasons. Discussing access by the authorities is not part of this article but also possible.
The most important protection methods provided by cryptography – without touching details – are: Encryption (Confidentiality), Protection against alteration (Integrity) and Identity protection (Authenticity). By now it should be clear why encryption alone is not a sufficient protection method - not for data privacy nor secure commuincation.
Should the algorithms used become broken and hence being unusable, our whole Internet communication would be insecure! The same is true for single connections that are not using secure channels!
Because of these algorithms (e.g.: RSA, AES, SHA-512, X.509v3), you – or more accurate your computer system – and your destination can communicate through other systems and still: the identity of the destination as well as the confidentiality and integrity of the data is guaranteed. Thus, the advantages like speed and reliability of the "best-effort" web can be used without losing communication security.
Nowadays, most websites and Internet portals operate primarily through HTTPS (hence TLS/SSL). This is even true for small sites, blogs and shops. Thanks to the easy usage and configuration of TLS/SSL certificates at hosting providers and thanks to Google, since websites with HTTPS connection are reportedly preferred on the list of search results. E-mails are transmitted using secure connections as well – but especially across borders you cannot be sure. The whole chain of e-mail gateways has to use secure connections to keep your communication secure. Most instant messengers also use TLS/SSL and some even end-to-end encryption.
In practice, many technical details have to be considered, like the correct configuration of algorithms (mostly server- but also client-sided). Special applications like e-mail have additional requirements. You have to be aware that every mail provider has full access to your e-mails because they have to forward e-mails to its destination address. However, at least the transmission between all other Internet components is (hopefully) secured. Advanced solutions for these applications (e-mail, messenger etc.) are based on "end-to-end encryption" which is not part of this article.
Summary

About the author
Computer Scientist Frank Hissen has over 26 years experience in IT and Development projects. He works as a freelance consultant for enterprises and companies of all sizes and is specialized in application security & compliance as well as cryptography/encryption.
Keywords
Internet Security, Data Security, Data Privacy, Computer Security, IT Security Awareness, Cryptography, Encryption, Background Knowledge