CrococryptFile official Download

CrococryptFile is freeware and open-source. It is free software without registration, without activation, without limitations and without ads.
CrococryptFile comes in different editions for different platforms. CrococryptFile currently includes support for English, Russian and German.
Windows
CrococryptFile runs on Windows even without installation - which might be helpful if you simply want to decrypt a *.croco archive that has been sent to you.
However, a smooth usage of CrococryptFile can only be guaranteed by using an installer, because only the installer versions provide Explorer integration.
Don't worry, there is an uninstaller included that removes CrococryptFile from your Windows installation if you want to.
CrococryptFile runs on all Windows versions from Windows XP to Windows 10.
Full Installer (no system requirements)
The easiest and recommended download for Windows users.
Application-only Installer (Java 1.7++ required)
Application-only package (Java 1.7++ required)
Linux and Mac (Java 1.7++ required)
Simply call the script "croco" after you extraced the archive. Mac is untested at the moment!
WebDecrypt
The WebDecrypt application also runs on all platforms running Java 1.7++. Simply call run.bat or run.sh after you extraced the archive.
This application also runs on a free instance of Google's App Engine (GAE): CrococryptFile WebDecrypt.
Offline Training Course
We also offer a CrococryptFile training course as free offline portable Windows application. Please note that it contains HD video. Hence, the portable extractor setup is ~125MB in size and the extracted application needs ~250MB of disk space.
Sources
The sources of the application itself (same for Windows, Linux, Mac) and the WebDecrypt web application can be found on GitHub:
https://github.com/fhissen/CrococryptFile.
Current AV Warnings
From time to time products of the Crococrypt Product Family are detected by individual antivirus software products as malware. These messages are so called "false positives". In such cases, you receive a warning by mistake because some binary pattern in the heuristics database of your antivirus software matches some random pattern in our product.
You can always verify that it is indeed a false warning by using, e.g., VirusTotal to scan our website or software. Sometimes even the whole website might be listed as malicious by SINGLE services.
If you are affected by such a case, please inform us via e-mail. We have and will correspond with the respective AV manufacturer which usually updates its virus pattern database.
The are no known warnings at the moment.
Windows 10/11 Installation Issue


Also, warnings when downloading in browser are possible:

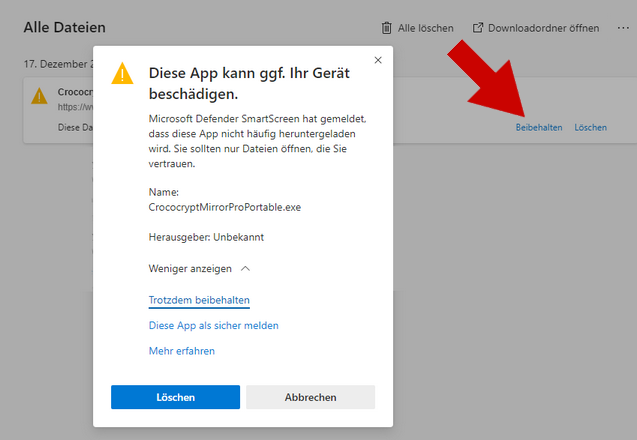


Version History
1.6 (05/13/2017):
- New: Support for Russian added (Special thanks to Aleksey Cheremnykh / Алексей Черемных)
1.5 (01/13/2017):
- New: Three new crypto suites have been integrated. Now, for PBKDF2-based encryption the algorithms Twofish, Serpent, and Camellia are also included.
- New: The hash iteration counter following PBKDF2 (password-based encryption) can now optionally be set by the user (this is backward compatible)
- Fix: UI workflow improvements regarding the progress window (e.g., in case the key generation takes a long time)
1.4 (02/22/2016):
- Fix: Performance improvement due to an internal buffer which was too small. In some cases, the data transfer rate could drop to 1 MB/s (e.g., on exFAT).
- Fix: Under unclarified circumstances, it could happen that no file dialogs appear.
1.3i (02/10/2016):
- Fix: This is a minor security update because of a NSIS installer security fix (Windows-Setup only). The application has not changed.
1.3 (07/02/2015):
- New: Additional crypto suite "cloaked" (headerless) archives using password based, cascading encryption with AES-256 and Twofish-256
1.2 (06/25/2015):
- New: Support for GPG/OpenPGP keys
1.0 (05/06/2015):
- First Release
License
This software and its source code is provided 'as-is', without any express or implied warranties or conditions of any kind, and is licensed under the GPLv3.
3rd-Party Products
The following 3rd-party software is used or embedded in compliance with their respective licenses (in alphabetical order). All trademarks and software are the property of their respective owners.
- Apache Commons, http://commons.apache.org/
- Bouncy Castle Crypto Provider, http://www.bouncycastle.org/
- Java and the Java Runtime from Oracle, http://www.oracle.com/technetwork/java/javase/terms/license
- Jetty Webserver, http://www.eclipse.org/jetty/licenses.php