Welcome to the official CrococryptFile Homepage:
An Open-source File encryption
News:
Windows 11 Certificate-based File Encryption (CrococryptFile with Hardware/Software Token)
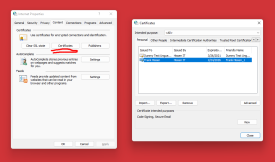 HissenIT's CrococryptFile fully supports Windows 11 including crypto suites. Besides classical end-user password-based encryption of files and folders, also the Windows Keystore using certificate tokens can be used. Hence, existing PKI infrastructure components can be used to encrypt file archives quickly also in business groups. ...
HissenIT's CrococryptFile fully supports Windows 11 including crypto suites. Besides classical end-user password-based encryption of files and folders, also the Windows Keystore using certificate tokens can be used. Hence, existing PKI infrastructure components can be used to encrypt file archives quickly also in business groups. ...
HissenIT Crococrypt Product Family Status of 2021 (Quo vadis?)
 Also upon some user requests, we describe the current status of our Crococrypt Product Family in 2021 which includes our file encryption software CrococryptFile and CrococryptMirror as well as the CrococryptLib SDK for secure password handling and easy-to-use password-based encryption in tailor-made applications. To cut it short: All programs are still in active development and you receive support! ...
Also upon some user requests, we describe the current status of our Crococrypt Product Family in 2021 which includes our file encryption software CrococryptFile and CrococryptMirror as well as the CrococryptLib SDK for secure password handling and easy-to-use password-based encryption in tailor-made applications. To cut it short: All programs are still in active development and you receive support! ...
HissenIT reaches over 15,000 Online Students on e-Learning Platform Udemy
 Over 700 worldwide reviews, with course ratings of 4.3 in average out of 5.0 of all courses (and I am working on it). At the moment, seven courses about IT Security Management, Secure custom Development, Cryptography and Encryption (English/German). Individual Coachings, Topics or online Seminars are possible as well. Courses can be licensed in other formats, like SCORM, for enterprise and offline use. ...
Over 700 worldwide reviews, with course ratings of 4.3 in average out of 5.0 of all courses (and I am working on it). At the moment, seven courses about IT Security Management, Secure custom Development, Cryptography and Encryption (English/German). Individual Coachings, Topics or online Seminars are possible as well. Courses can be licensed in other formats, like SCORM, for enterprise and offline use. ...
Introduction

CrococryptFile is a file encryption tool which creates encrypted archives of arbitrary files and folders.
Features
The encryption features of CrococryptFile can be compared to a ZIP utility that uses ZIP's AES encryption. However, there are significant differences. CrococryptFile...
- encrypts all file and folder information including filenames, time/date and filesize information,
- disguises any information of the archive's content, because all data and meta-data is simply integrated into a giant file dump.
A *.croco file solely shows that it is indeed a CrococryptFile archive and which crypto suite (e.g., password-based AES-256 encryption) is used.
Moreover, headerless or cloaked files are supported. Using a freely selectable iteration count in case of password-based encryption, this is especially useful for, e.g., file backups or file archives stored in Cloud storage.
Open
CrococryptFile and all its clients are open-source. The GitHub repository can be checked out here.
CrococryptFile is based on the Java technology to enable maximum flexibility for arbitrary platform use cases including clients and servers.
Use Cases
Please see the gallery for the best way to start getting an impression of the functions of CrococryptFile.
CrococryptFile currently runs under Windows (XP and up), Linux, Mac (untested) and offers a Web-based decryption application.
Moreover, CrococryptFile has a commandline interface that can be used without any GUI, to trigger the GUI or to be used in scripts. CrococryptFile does not need a GUI operating system. Its API or commandline interface can also be used on servers or in applications.
Windows: Explorer integration
By using the Windows-Setup CrococryptFile becomes integrated into the Windows Explorer context menu (vgl. Screenshots). Multiple files and directories can be selected at once and by using the context menu option Send to... can be save to a single archive by CrococryptFile. It ships also with an uninstaller which cleans your Windows installation from CrococryptFile if you wish.
WebDecrypt
The Web-based decryption application in its default set-up is running on a free instance of Google's App Engine (GAE):
CrococryptFile WebDecrypt.
The WebDecryptor is stateless, does not cache files, has no database and is no file exchange platform. It is simply a web-based version of the decryption mechanism of CrococryptFile. It can be used to send encrypted archives to other people and offer an easy way to decrypt these. At the moment, only password-based encryption suites are supported for the WebDecryptor. The GAE version limits uploaded files to 10MB.
If you are a company or don't trust this installation, you can download a standalone-version of WebDecrypt which is based on the Jetty Webserver. Don't forget to enable TLS/SSL. Moreover, you can use the open-source WebDecrypt Java servlet package to integrate it into your own application.
Note: The GAE installation is unfortunately a bit slow regarding cryptographic operations.
Cryptography
The architecture of CrococryptFile does not limit the trust anchor technology to just password protected files. In fact, any trust source can be implemented and used. For instance under Windows, X.509 RSA certificates if featured in the Windows keystore can be used to create an encrypted archive. In the future, other technologies might be integrated, like PKCS #11. Although the default encryption algorithm is AES, CrococryptFile is not limited to use only AES in future versions.
When password-based encryption is used, the default implementation uses PKCS #5 (PBKDF2) with a SHA512-HMAC and currently strong 100000 iterations as default setting. However, the user is able to choose the number of iterations as well. The iteration count is not hard-coded in the software but written into the archive. Hence, future changes allow for enhanced or user-based iteration counts by still being downward compatible.
If you are interested in details about the encryption scheme, please take a look at the sources. The short description would be the following. Every .croco-archive is (currently) encrypted using AES-256. The file index and all included files/folders are completely encrypted using AES in CBC mode. For each new archive, a new AES key is generated. This key is then encrypted using a trust anchor, like a PBE or an RSA certificate (Windows). So basically, a .croco-archive starts with a plain header (info about the file and the crypto suite, e.g., PBE), an encrypted header (including the AES key), the encrypted dump of files, and the encrypted index.
Crypto Suites
The following crypto suites are currently included:
- Password-based encryption (following PBKDF2) with AES-256
- Password-based encryption (following PBKDF2) with Twofish-256
- Password-based encryption (following PBKDF2) with Serpent-256
- Password-based encryption (following PBKDF2) with Camellia-256
- Windows Keystore based encryption using RSA keys and AES-256
- GPG/OpenPGP key based encryption with AES-256
- Cloaked (headerless) Password based Encryption (AES-Twofish-256)
- Cloaked (headerless) Password based Encryption (AES-Twofish-256) padded to multiples of 1MB but also allows for arbitrary size
We have written a short article to describe how cloaked files work.
Potential Features / Roadmap
The following features are possible for future versions:
Backlog
- Android app
- PKCS #11 support: Hardware tokens/SmartCards via P11
- Integrating keyfiles: Although, e.g., PKCS12 files can be used under Windows via the CAPI encryption suite, general/native keyfile support would be great for different formats.
- File filter: Optional mode to exclude files with certain filename patterns
- Digital Signatures: Integrate digital signatures into archives (single, groups)
- Crypto settings: Offer the user to choose between algorithms and options to create preferred cryptographic settings
- SMB/CIFS support: Server version of CrococryptFile (maybe including group encryption) based on SMB/CIFS
Further Documentation
We created a free Video-based Training Course about the usage of CrococryptFile and a little background on encryption basics.
Commercial Support
Are you seeking commercial support? Feel free to contact us and talk about corresponding possibilities for your case: Contact.
Share
![]() Please like and share the Facebook page to spread the product if you like it! This encourages the further development!
Please like and share the Facebook page to spread the product if you like it! This encourages the further development!
Keywords
encryption, PKI, public key, certicates, x509, password security, password based encryption, file encryption, group encryption, PGP, GnuPG, public key, symmetric encryption