Blog ►
HissenIT Blog & News - IT, Computer, Programming, Development, Security
You can follow this blog through this news feed or our social media channels.
Previous publications can be found in the publication archive.
“Many developers lack the essential knowledge and skills to effectively implement secure software development” [News]
 Online Security Courses and more time for security in software development projects as one step into the right direction. Security has to be implemented from the beginning. Project managers have to provide enough development time on non-functional features or make security a functional feature.
...
Online Security Courses and more time for security in software development projects as one step into the right direction. Security has to be implemented from the beginning. Project managers have to provide enough development time on non-functional features or make security a functional feature.
...
IT Security Awareness Training for Employees to follow ISO/IEC 27001 & 27002 and facilitate Audits [News]
 Online training or Intranet-based Learning Management Systems (LMS) are two approaches to implement regular and accountable IT security awareness training for employees. This is true for companies of all sizes and all departments. One can find reliable, comprehensive courses for general Computer, Internet and E-Mail users as well as developers or project managers. Using e-learning approaches offers executives to monitor and document the learning progress and success of their employees easily and thus prove in security audits that adequate IT and information security awareness training for employees has been conducted.
...
Online training or Intranet-based Learning Management Systems (LMS) are two approaches to implement regular and accountable IT security awareness training for employees. This is true for companies of all sizes and all departments. One can find reliable, comprehensive courses for general Computer, Internet and E-Mail users as well as developers or project managers. Using e-learning approaches offers executives to monitor and document the learning progress and success of their employees easily and thus prove in security audits that adequate IT and information security awareness training for employees has been conducted.
...
IT Security Awareness for Employees - Lecture E-Mail Security (e-Learning) [News]
 E-Mail Security online video lecture for Employees - Learn what to look out for when using E-Mails. This is a full lecture that is part of the Online Training Course "IT Security Awareness for Employees and Individuals - The pragmatic complete Guide to Internet and Computer Security".
...
E-Mail Security online video lecture for Employees - Learn what to look out for when using E-Mails. This is a full lecture that is part of the Online Training Course "IT Security Awareness for Employees and Individuals - The pragmatic complete Guide to Internet and Computer Security".
...
(Shorts) IT Security Awareness for Employees e-Learning - Lecture Quishing [News]
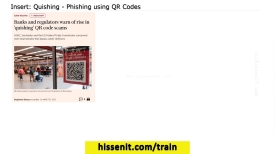 Cyber Security Training Excerpt: Quishing – Phishing using QR Codes
...
Cyber Security Training Excerpt: Quishing – Phishing using QR Codes
...
HissenIT InvoiceCreator and ParcelConnector - IT Solutions for small and medium-sized Businesses [News]
 In addition to custom development and consulting services for SMEs in the field of data exchange, maintenance, evaluation and preparation as well as import & export especially in the sector of e-commerce, HissenIT also offers ready-to-use applications that enable technically skilled users with little or no support to integrate solutions for invoice and document creation as well as DHL parcel label generation into existing systems and individual work processes.
...
In addition to custom development and consulting services for SMEs in the field of data exchange, maintenance, evaluation and preparation as well as import & export especially in the sector of e-commerce, HissenIT also offers ready-to-use applications that enable technically skilled users with little or no support to integrate solutions for invoice and document creation as well as DHL parcel label generation into existing systems and individual work processes.
...
Understanding CSV Files: What they are and how to use (How-to) [Background articles]
 Using CSV files is a daily routine for many people who have to accomplish a - fully automatic or semiautomatic - data exchange between different IT systems. CSV files are not the only solution path, but are very common. This concerns for instance online and e-commerce businesses which import the current orders from eBay into their own ERP system (Enterprise Resource Planning) or the accounting when exporting tax data to the tax office.
...
Using CSV files is a daily routine for many people who have to accomplish a - fully automatic or semiautomatic - data exchange between different IT systems. CSV files are not the only solution path, but are very common. This concerns for instance online and e-commerce businesses which import the current orders from eBay into their own ERP system (Enterprise Resource Planning) or the accounting when exporting tax data to the tax office.
...
Windows 11 Certificate-based File Encryption (CrococryptFile with Hardware/Software Token) [IT Security]
 HissenIT's CrococryptFile fully supports Windows 11 including crypto suites. Besides classical end-user password-based encryption of files and folders, also the Windows Keystore using certificate tokens can be used. Hence, existing PKI infrastructure components can be used to encrypt file archives quickly also in business groups.
...
HissenIT's CrococryptFile fully supports Windows 11 including crypto suites. Besides classical end-user password-based encryption of files and folders, also the Windows Keystore using certificate tokens can be used. Hence, existing PKI infrastructure components can be used to encrypt file archives quickly also in business groups.
...
HissenIT ParcelConnector to easily integrate DHL Shipping Solutions published [News]
 Using the solutions "ParcelConnector" and "Desktop-ParcelConnector" companies can integrate the purchase of DHL shipping product labels including customs declarations into their own sales process.
...
Using the solutions "ParcelConnector" and "Desktop-ParcelConnector" companies can integrate the purchase of DHL shipping product labels including customs declarations into their own sales process.
...
(Briefly) Backups - Do we need that? [Background articles]
HissenIT Crococrypt Product Family Status of 2021 (Quo vadis?) [News]
 Also upon some user requests, we describe the current status of our Crococrypt Product Family in 2021 which includes our file encryption software CrococryptFile and CrococryptMirror as well as the CrococryptLib SDK for secure password handling and easy-to-use password-based encryption in tailor-made applications. To cut it short: All programs are still in active development and you receive support!
...
Also upon some user requests, we describe the current status of our Crococrypt Product Family in 2021 which includes our file encryption software CrococryptFile and CrococryptMirror as well as the CrococryptLib SDK for secure password handling and easy-to-use password-based encryption in tailor-made applications. To cut it short: All programs are still in active development and you receive support!
...
HissenIT reaches over 15,000 Online Students on e-Learning Platform Udemy [News]
 Over 700 worldwide reviews, with course ratings of 4.3 in average out of 5.0 of all courses (and I am working on it). At the moment, seven courses about IT Security Management, Secure custom Development, Cryptography and Encryption (English/German). Individual Coachings, Topics or online Seminars are possible as well. Courses can be licensed in other formats, like SCORM, for enterprise and offline use.
...
Over 700 worldwide reviews, with course ratings of 4.3 in average out of 5.0 of all courses (and I am working on it). At the moment, seven courses about IT Security Management, Secure custom Development, Cryptography and Encryption (English/German). Individual Coachings, Topics or online Seminars are possible as well. Courses can be licensed in other formats, like SCORM, for enterprise and offline use.
...
Please understand: Secure Programming is not 'Hacking' (Skillshare)! [News]
 Usually, you won’t find blog posts like this one from me. They are kind of off-topic. I will definitely put it in the ‘news’ section only...
...
Usually, you won’t find blog posts like this one from me. They are kind of off-topic. I will definitely put it in the ‘news’ section only...
...
Secure Programming of Web Applications: Authentification [IT Security]
 We can read about numerous successful attacks on well-known web applications on a weekly basis. Reason enough to study the background of "Web Application Security" of custom-made / self-developed applications - no matter if these are used only internally or with public access.
...
We can read about numerous successful attacks on well-known web applications on a weekly basis. Reason enough to study the background of "Web Application Security" of custom-made / self-developed applications - no matter if these are used only internally or with public access.
...
Secure Programming of Web Applications: Session-Hijacking [IT Security]
 We can read about numerous successful attacks on well-known web applications on a weekly basis. Reason enough to study the background of "Web Application Security" of custom-made / self-developed applications - no matter if these are used only internally or with public access.
...
We can read about numerous successful attacks on well-known web applications on a weekly basis. Reason enough to study the background of "Web Application Security" of custom-made / self-developed applications - no matter if these are used only internally or with public access.
...
Secure Programming of Web Applications: Clickjacking [IT Security]
 We can read about numerous successful attacks on well-known web applications on a weekly basis. Reason enough to study the background of "Web Application Security" of custom-made / self-developed applications - no matter if these are used only internally or with public access.
...
We can read about numerous successful attacks on well-known web applications on a weekly basis. Reason enough to study the background of "Web Application Security" of custom-made / self-developed applications - no matter if these are used only internally or with public access.
...
Secure Programming of Web Applications: Remote File Inclusion (RFI) and Local File Inclusion (LFI) resp. Directory/Path Traversal [IT Security]
 We can read about numerous successful attacks on well-known web applications on a weekly basis. Reason enough to study the background of "Web Application Security" of custom-made / self-developed applications - no matter if these are used only internally or with public access.
...
We can read about numerous successful attacks on well-known web applications on a weekly basis. Reason enough to study the background of "Web Application Security" of custom-made / self-developed applications - no matter if these are used only internally or with public access.
...
Secure Programming of Web Applications: Open Redirection [IT Security]
 We can read about numerous successful attacks on well-known web applications on a weekly basis. Reason enough to study the background of "Web Application Security" of custom-made / self-developed applications - no matter if these are used only internally or with public access.
...
We can read about numerous successful attacks on well-known web applications on a weekly basis. Reason enough to study the background of "Web Application Security" of custom-made / self-developed applications - no matter if these are used only internally or with public access.
...
Secure Programming of Web Applications: Cross-Site Scripting (XSS) [IT Security]
 We can read about numerous successful attacks on well-known web applications on a weekly basis. Reason enough to study the background of "Web Application Security" of custom-made / self-developed applications - no matter if these are used only internally or with public access.
...
We can read about numerous successful attacks on well-known web applications on a weekly basis. Reason enough to study the background of "Web Application Security" of custom-made / self-developed applications - no matter if these are used only internally or with public access.
...
Secure Programming of Web Applications: Cross-Site Request Forgery (CSRF) [IT Security]
 We can read about numerous successful attacks on well-known web applications on a weekly basis. Reason enough to study the background of "Web Application Security" of custom-made / self-developed applications - no matter if these are used only internally or with public access.
...
We can read about numerous successful attacks on well-known web applications on a weekly basis. Reason enough to study the background of "Web Application Security" of custom-made / self-developed applications - no matter if these are used only internally or with public access.
...
Secure Programming of Web Applications: SQL Code Injection [IT Security]
 We can read about numerous successful attacks on well-known web applications on a weekly basis. Reason enough to study the background of "Web Application Security" of custom-made / self-developed applications - no matter if these are used only internally or with public access.
...
We can read about numerous successful attacks on well-known web applications on a weekly basis. Reason enough to study the background of "Web Application Security" of custom-made / self-developed applications - no matter if these are used only internally or with public access.
...
Data Security through Cryptography - Interview with Frank Hissen [News]
 IT Security Expert and Computer Scientist Frank Hissen talking about cryptography and how cryptography helps to protect our data security during our private and professional everyday life.
...
IT Security Expert and Computer Scientist Frank Hissen talking about cryptography and how cryptography helps to protect our data security during our private and professional everyday life.
...
Internet Security: Why cryptography (and encryption) is essential [IT Security]
 Internet connections are no direct lines. Every intermediary component holds full access to your Internet traffic. That means: read, alter, redirect, discard. Or put another way: manipulate, record, log, render unusable.
...
Internet connections are no direct lines. Every intermediary component holds full access to your Internet traffic. That means: read, alter, redirect, discard. Or put another way: manipulate, record, log, render unusable.
...
CrococryptFile still in active development - Wipe function and more in preparation [News]
 With this quick post, we wanted to let users know that CrococryptFile is still in active development. We are busy with other (commercial) projects, hence, CrococryptFile has to wait a little bit for its new version. The new version will include the often requested wipe function, to securely delete encrypted files.
...
With this quick post, we wanted to let users know that CrococryptFile is still in active development. We are busy with other (commercial) projects, hence, CrococryptFile has to wait a little bit for its new version. The new version will include the often requested wipe function, to securely delete encrypted files.
...
HissenIT has reached more than 10,000 online students worldwide with in-depth IT security courses on Udemy [News]
 With more than 20 years of IT security and security training experience, HissenIT publishes also online trainings in the areas of application security, encryption and cryptography. Information technologies are the essential part of any business and a huge part in our private life. Hence, awareness of IT security on the technical level has become essential. Increased numbers of reports on cyber attacks and system vulnerabilities are one proof.
...
With more than 20 years of IT security and security training experience, HissenIT publishes also online trainings in the areas of application security, encryption and cryptography. Information technologies are the essential part of any business and a huge part in our private life. Hence, awareness of IT security on the technical level has become essential. Increased numbers of reports on cyber attacks and system vulnerabilities are one proof.
...
Computer security – Not "Update Flash Player" but "Remove Flash Player"
 In light of current events, many IT news pages create headlines like "Patch your Flash Player, now!". This happens – again and again – with regularity when a new vulnerability in Adobe Flash gets out or a corresponding security patch or update is published...
...
In light of current events, many IT news pages create headlines like "Patch your Flash Player, now!". This happens – again and again – with regularity when a new vulnerability in Adobe Flash gets out or a corresponding security patch or update is published...
...
Attention when choosing an Encryption solution - Weakness in Password manager of Firefox and Thunderbird [IT Security]
 An "IT security researcher" recently engaged attention on a seemingly older, known weakness in Mozilla's password managers of Firefox and Thunderbird. Core problem is the way of dealing with the master password (keyword: secure password hashing). We recommend for years to pay close attention - when choosing an encryption software - which password hashing procedure is used. Otherwise, you eventually have no real data encryption at all. We try to provide some clear background information.
...
An "IT security researcher" recently engaged attention on a seemingly older, known weakness in Mozilla's password managers of Firefox and Thunderbird. Core problem is the way of dealing with the master password (keyword: secure password hashing). We recommend for years to pay close attention - when choosing an encryption software - which password hashing procedure is used. Otherwise, you eventually have no real data encryption at all. We try to provide some clear background information.
...
HissenIT CrococryptMirror Pro v1.5 released - Software for encrypted File Backups [News]
 HissenIT introduced the Pro version of the file and folder backup encryption tool CrococryptMirror. To finance the freeware project, the new Pro version costs a small fee. New features of CrococryptMirror will always be introduced in the Pro version first. Version 1.5 received a massive performance enhancement due to internal optimization. Also, the UI was revised and several stability fixes were added. Still, the software works independent and does not require an online connection or registration.
...
HissenIT introduced the Pro version of the file and folder backup encryption tool CrococryptMirror. To finance the freeware project, the new Pro version costs a small fee. New features of CrococryptMirror will always be introduced in the Pro version first. Version 1.5 received a massive performance enhancement due to internal optimization. Also, the UI was revised and several stability fixes were added. Still, the software works independent and does not require an online connection or registration.
...
JavaFX WebView / WebKit error at JavaScript to Java communication (Java 8) [Development/Java]
 We are using Java for nearly two decades to build products. When an integrated WebKit was finally introduced to the Java platform - coming with JavaFX - development opportunities were boosted tremendously, because now you are able to integrate HTML5 web technologies into your desktop application easily.
...
We are using Java for nearly two decades to build products. When an integrated WebKit was finally introduced to the Java platform - coming with JavaFX - development opportunities were boosted tremendously, because now you are able to integrate HTML5 web technologies into your desktop application easily.
...
Missing the old User Interface (UI) Design Theme in new Firefox Quantum? [Computer Guides & Tips]
 By adjusting the Firefox configuration easily and manually, the 'feeling' of the old user interface theme can be restored a little bit on the basis of the new built-in default design. We show a design proposal and explain the easy installation.
...
By adjusting the Firefox configuration easily and manually, the 'feeling' of the old user interface theme can be restored a little bit on the basis of the new built-in default design. We show a design proposal and explain the easy installation.
...
CrococryptFile Offline Training Course as free Windows Software available [News]
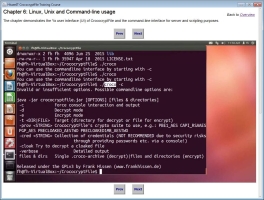 HissenIT published the existing and freely available online video training course "File Encryption Basics and Practices with CrococryptFile" now also as offline version as a portable Windows software - using its in-house application framwork. Since it contains HD video, the portable extractor setup is ~125MB in size and the extracted application needs ~250MB of disk space.
...
HissenIT published the existing and freely available online video training course "File Encryption Basics and Practices with CrococryptFile" now also as offline version as a portable Windows software - using its in-house application framwork. Since it contains HD video, the portable extractor setup is ~125MB in size and the extracted application needs ~250MB of disk space.
...
HissenIT releases freeware for master data management [News]
 The new Windows software is called “HissenIT Masterdata”. It is an easy-to-use master data management software. Besides common basic data, the software stores any number of addresses and other contact data of people or companies. An arbitrary number ob custom data fields can be defined as well.
...
The new Windows software is called “HissenIT Masterdata”. It is an easy-to-use master data management software. Besides common basic data, the software stores any number of addresses and other contact data of people or companies. An arbitrary number ob custom data fields can be defined as well.
...
Open-source File encryption software CrococryptFile 1.5 released - New crypto suites and crypto settings [News]
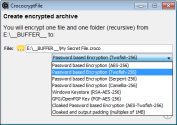 HissenIT released a new version of the file archive encryption tool CrococryptFile. Three new crypto suites using Twofish, Serpent, and Camellia are included. Moreover, the hash iteration count in case of password-based encryption following PBKDF2 is now selectable by the user (which is backward compatible).
...
HissenIT released a new version of the file archive encryption tool CrococryptFile. Three new crypto suites using Twofish, Serpent, and Camellia are included. Moreover, the hash iteration count in case of password-based encryption following PBKDF2 is now selectable by the user (which is backward compatible).
...
File and Folder encryption software CrococryptMirror 1.4 released - New password features and stability improvements [News]
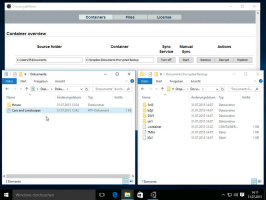 HissenIT released a new version of the file and folder encryption tool CrococryptMirror. It includes a password change function and - as requested by many users - a command-line option to provide the keyfile password. Although not recommended, this function can be used to provide the password, e.g., in scripts for automation purposes. The feature can also be used to "store" the keyfile password.
...
HissenIT released a new version of the file and folder encryption tool CrococryptMirror. It includes a password change function and - as requested by many users - a command-line option to provide the keyfile password. Although not recommended, this function can be used to provide the password, e.g., in scripts for automation purposes. The feature can also be used to "store" the keyfile password.
...
"IT Security for Project Managers" now also as Kindle e-Book [News]
 Our Whitepaper/Guideline is now also available as e-book for Amazon's Kindle (English/German).
...
Our Whitepaper/Guideline is now also available as e-book for Amazon's Kindle (English/German).
...
German PCWorld counterpart recommends CrococryptFile in online article [News]
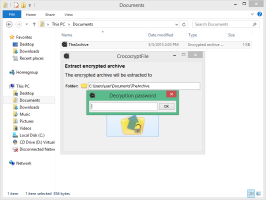 In the article called "Security Tools: Secure Windows 10", CrococryptFile is shortly described and recommended.
...
In the article called "Security Tools: Secure Windows 10", CrococryptFile is shortly described and recommended.
...
IT Security for Project Managers: About implementing security in IT projects properly – A Guideline [News]
 Despite many accepted IT security standards, many IT projects fail at IT security. What needs to be considered, what mistakes and pitfalls to avoid.
...
Despite many accepted IT security standards, many IT projects fail at IT security. What needs to be considered, what mistakes and pitfalls to avoid.
...
HissenIT published Application Security and Cryptography Online Trainings [News]
 Reports on cyber attacks have increased tremendously over the last years. Information technologies are the essential part of any business and a huge part in our private life. Hence, awareness of IT security on the technical level has become very important – for developers and decision makers alike.
...
Reports on cyber attacks have increased tremendously over the last years. Information technologies are the essential part of any business and a huge part in our private life. Hence, awareness of IT security on the technical level has become very important – for developers and decision makers alike.
...
Video Tutorial: File Encryption Basics and Practices with CrococryptFile [News]
 In this course, you will learn how to use CrococryptFile, the open-source file encryption solution. Learn what encryption means on the technical level – as a background information to choose the right file encryption method for your case. If you care about privacy and if you are willing to do something about it, you are already on the right track. This applies for enterprise and private users alike.
...
In this course, you will learn how to use CrococryptFile, the open-source file encryption solution. Learn what encryption means on the technical level – as a background information to choose the right file encryption method for your case. If you care about privacy and if you are willing to do something about it, you are already on the right track. This applies for enterprise and private users alike.
...
CrococryptMirror 1.2 released – 32bit support and bugfixes [News]
 We released an update of CrococryptMirror as version 1.2. This relates to the setup and the portable version. Beside some bugfixes, we added a 32bit version for Windows XP and above.
...
We released an update of CrococryptMirror as version 1.2. This relates to the setup and the portable version. Beside some bugfixes, we added a 32bit version for Windows XP and above.
...
Say no to plain passwords: Secure Password Hashing [IT Security]
 Plaintext passwords should not be used anymore. You are probably using a web shop software framework that takes already care of this. Most application frameworks in the world do not use plain passwords anymore but password hashes instead.
...
Plaintext passwords should not be used anymore. You are probably using a web shop software framework that takes already care of this. Most application frameworks in the world do not use plain passwords anymore but password hashes instead.
...
Encryption background: What is key wrapping? [IT Security]
 Key wrapping is a simple technique in cryptography that is used in almost all common encryption technologies.
...
Key wrapping is a simple technique in cryptography that is used in almost all common encryption technologies.
...
Open-Source and Security: Why Open-Source is not insecure [IT Security]
 Recently, I received the question if it would not be dangerous, when the source code for an encryption software is publicly available. An answer...
...
Recently, I received the question if it would not be dangerous, when the source code for an encryption software is publicly available. An answer...
...
Password-based Encryption made easy [IT Security]
Easy encryption for Android apps – CrococryptLib 1.4 released [News]
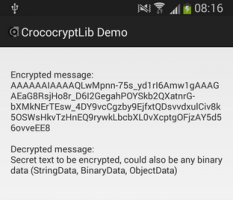 CrococryptLib 1.4 for Android released: A library for mobile apps that allows the most easiest integration of password-based encryption, hashes and other cryptography operations. No in-depth cryptography knowledge is required to integrate encryption into Android apps.
...
CrococryptLib 1.4 for Android released: A library for mobile apps that allows the most easiest integration of password-based encryption, hashes and other cryptography operations. No in-depth cryptography knowledge is required to integrate encryption into Android apps.
...
The easiest way to integrate encryption into enterprise applications – HissenIT released CrococryptLib [News]
 HissenIT recently released CrococryptLib for Java: A library for Java back-end, desktop and mobile applications that allows the most easiest integration of encryption and other cryptography operations. No in-depth cryptography knowledge is required to integrate encryption into
enterprise applications or software products.
...
HissenIT recently released CrococryptLib for Java: A library for Java back-end, desktop and mobile applications that allows the most easiest integration of encryption and other cryptography operations. No in-depth cryptography knowledge is required to integrate encryption into
enterprise applications or software products.
...
CrococryptMirror and CrococryptFile ready for Windows 10 [News]
 We were able to test CrococryptMirror and CrococryptFile on Windows 10 successfully. Both applications run without problems in their respective current versions.
...
We were able to test CrococryptMirror and CrococryptFile on Windows 10 successfully. Both applications run without problems in their respective current versions.
...
Introducing cloaked (headerless) files - CrococryptFile 1.3 released [News]
 Today, we released CrococryptFile 1.3 as free download. This version includes a new crypto suite: "cloaked" archives. This kind of suite encrypts archives without headers. What this exactly means, we explain in the following.
...
Today, we released CrococryptFile 1.3 as free download. This version includes a new crypto suite: "cloaked" archives. This kind of suite encrypts archives without headers. What this exactly means, we explain in the following.
...
CrococryptFile 1.2 released – GPG/OpenPGP keys are now supported [News]
 We released CrococryptFile 1.2 today. This version includes support for GPG/OpenPGP keyrings which can be used as an additional crypto suite. Multiple recipients for an encrypted archive are also supported.
...
We released CrococryptFile 1.2 today. This version includes support for GPG/OpenPGP keyrings which can be used as an additional crypto suite. Multiple recipients for an encrypted archive are also supported.
...
Container vs. File-by-file Encryption OR CrococryptFile vs. CrococryptMirror [IT Security]
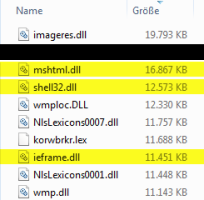 This article is about the differences of the encryption schemes between a container and a file-by-file encryption solution and the resulting privacy implications. At the end, you will see that it is also a matter of taste and application context.
...
This article is about the differences of the encryption schemes between a container and a file-by-file encryption solution and the resulting privacy implications. At the end, you will see that it is also a matter of taste and application context.
...
CrococryptFile – GnuPG keyfile support as Kickstarter project [News]
 Open-source file encryption CrococryptFile as Kickstarter project
...
Open-source file encryption CrococryptFile as Kickstarter project
...
HissenIT released CrococryptFile – An open-source file encryption software [News]
 HissenIT recently released an open-source file encryption software called CrococryptFile.
...
HissenIT recently released an open-source file encryption software called CrococryptFile.
...